Exploiting and Mitigating an XSS Vulnerability in GetBoo (OWASP BWA)
📌 Introduction
Cross-Site Scripting (XSS) is one of the most common web vulnerabilities, allowing attackers to inject malicious scripts into web pages viewed by other users. While testing GetBoo, an application in the OWASP Broken Web Applications Project, you can find a reflected XSS vulnerability in the search feature.
In this post, I’ll demonstrate how I identified the issue and, most importantly, how to mitigate it to help developers build more secure applications.
🔍 Finding the Vulnerability
While using the Discover search feature, I noticed the input was being reflected on the page. Initially, trying basic JavaScript injection like:


…did not work because it was escaped in the output.
However, when inspecting the source code (F12), I found that my input was embedded inside an <input> field’s value="" attribute:
🔐 How to Fix It (Mitigation Strategies)
To prevent this type of attack, developers should:
✅ Properly Encode User Input
In PHP, use:
Disclaimer
The information shared in this blog is for educational and informational purposes only. It is intended to help individuals learn and experiment with cybersecurity concepts in a controlled, legal, and ethical manner. I do not condone or support the use of any tools or techniques for illegal activities. Readers are responsible for ensuring that they use this information in compliance with all applicable laws and regulations.
Please note that while the tools and concepts discussed are already publicly available at other sites and widely used within the cybersecurity community, it is crucial to always practice cybersecurity skills responsibly and ethically. Any misuse of this information is solely the responsibility of the reader. I am not liable for any consequences that may arise from the use of the information provided here. The code examples provided here are condensed and summarized on purpose for the reason above.
This was a key observation! Since user input was directly injected into an HTML attribute, I realized I might be able to break out of the attribute and execute JavaScript.
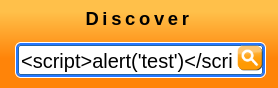
By entering:
…I successfully triggered a JavaScript popup, confirming the presence of an XSS vulnerability.
✅ Use Content Security Policy (CSP)
A CSP header helps prevent inline JavaScript execution:
✅ Input Validation
Only allow expected characters:
By implementing these measures, developers can protect applications from XSS attacks, making the web a safer place for users.
Let’s work together to make the internet more secure! 🚀