A Weekend with Python’s Socket Library: Exploring Cybersecurity Applications
As someone passionate about cybersecurity, I recently realized there was a gap in my knowledge: the Python socket library. While I had a solid grasp of Python for general scripting, I had never explored how it could be applied to network programming—something crucial for system security and penetration testing. Determined to change that, I spent a weekend diving deep into the world of sockets, exploring their applications in cybersecurity.
Understanding the Basics: What Are Sockets?
At its core, a socket is an endpoint for communication between two machines over a network. Python's socket library provides a simple interface to work with sockets, enabling everything from simple message exchanges to complex network tools.
My First Steps with Sockets
I started with the fundamentals: creating a basic TCP client and server. Here’s a small snippet of the TCP client that connects to a server and exchanges messages:


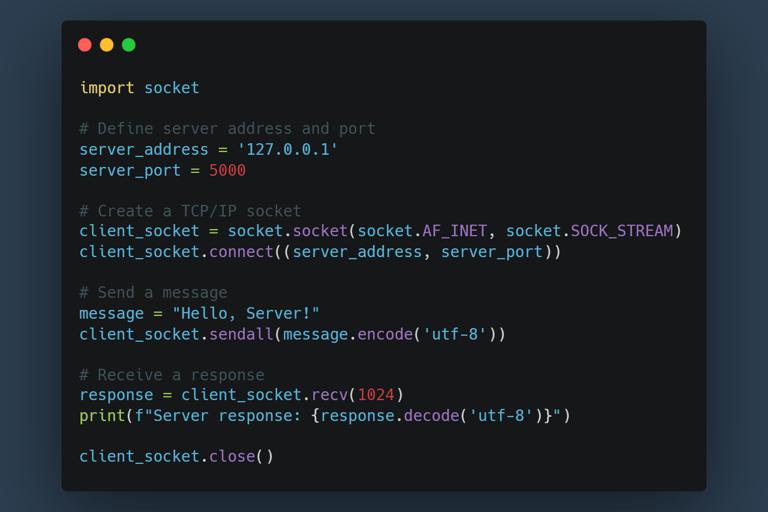
This simple client-server interaction opened my eyes to the versatility of the socket library. From here, I was ready to explore more practical, cybersecurity-focused applications.
From Basics to Cybersecurity: Building Practical Tools
Port Scanner
One of the first tools I built was a port scanner, designed to probe a target machine for open ports. Port scanning is a foundational task in penetration testing, used to identify active services on a system. While powerful tools like Nmap already exist for this purpose, my goal for the weekend was to deepen my understanding of how such tools work behind the scenes. Here’s a simplified version of the scanner:
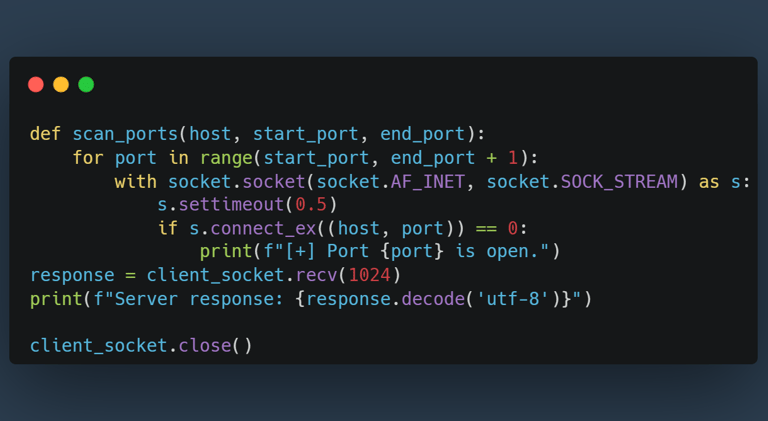
Running this tool on my Metasploitable VM gave me hands-on experience while ensuring I stayed ethical and within my private network.
Vulnerability Tester
The next step was building a basic vulnerability tester, which scans for default credentials on services like FTP and SSH. This tool expanded my understanding of how misconfigurations and weak credentials can expose systems to attacks. Using Python libraries like ftplib and paramiko, I implemented logic to test common username-password combinations.
Learning in Tandem
To complement my hands-on practice, I enrolled in a Udemy course on creating penetration testing tools with Python. This structured learning not only reinforced my experiments but also introduced me to best practices for building penetration testing tools. I had the opportunity to code a backdoor and a server from scratch, which allowed me to better understand how tools, like those found in the Metasploit Framework within Kali Linux, function. Building my own tools has given me deeper insights into how these attacks are executed in real-world scenarios. Additionally, this experimentation led to several "ah-ha" moments, including the realization that Linux native tools, like arping, can be used to emulate man-in-the-middle attacks through ARP spoofing.
Key Takeaways
The Power of Python for Cybersecurity:
Python’s simplicity and extensive libraries make it ideal for building cybersecurity tools.
Ethical Practices:
Tools like port scanners and vulnerability testers must be used responsibly. Testing within a controlled environment, like a Metasploitable VM, ensures legality and ethical integrity.
The Importance of Foundations:
Starting with the basics of the socket library was crucial. It gave me the confidence to tackle more advanced topics like threading and service enumeration.
What’s Next?
This journey has only scratched the surface of what’s possible with Python in cybersecurity. My future plans include expanding my skills by:
Building a basic intrusion detection system (IDS) to monitor and analyze network traffic for potential threats.
Creating a custom packet sniffer to capture and examine network packets.
Exploring integration with advanced libraries like Scapy for more powerful and flexible network analysis.
Integrating past learnings with tools like Wireshark to enhance packet analysis, which has already proven invaluable in my professional career for network troubleshooting.
Developing a Modbus TCP/IP client to emulate and understand how ICS (Industrial Control Systems) testing tools like ModScan operate. Although this isn’t directly penetration testing, it aligns with my interest in learning more about ICS network security.
I’ll continue documenting my learning and projects here, so stay tuned for more deep dives into Python and system security.
Closing Thoughts
For anyone starting with Python’s socket library or looking to get into cybersecurity, my advice is simple: start small, build practical tools, and always test ethically. The combination of curiosity, hands-on practice, and structured learning will take you to the next level!
Feel free to share your thoughts or questions with me. Let’s learn together!
Disclaimer
The information shared in this blog is for educational and informational purposes only. It is intended to help individuals learn and experiment with cybersecurity concepts in a controlled, legal, and ethical manner. I do not condone or support the use of any tools or techniques for illegal activities. Readers are responsible for ensuring that they use this information in compliance with all applicable laws and regulations.
Please note that while the tools and concepts discussed are already publicly available at other sites and widely used within the cybersecurity community, it is crucial to always practice cybersecurity skills responsibly and ethically. Any misuse of this information is solely the responsibility of the reader. I am not liable for any consequences that may arise from the use of the information provided here. The code examples provided here are condensed and summarized on purpose for the reason above.
